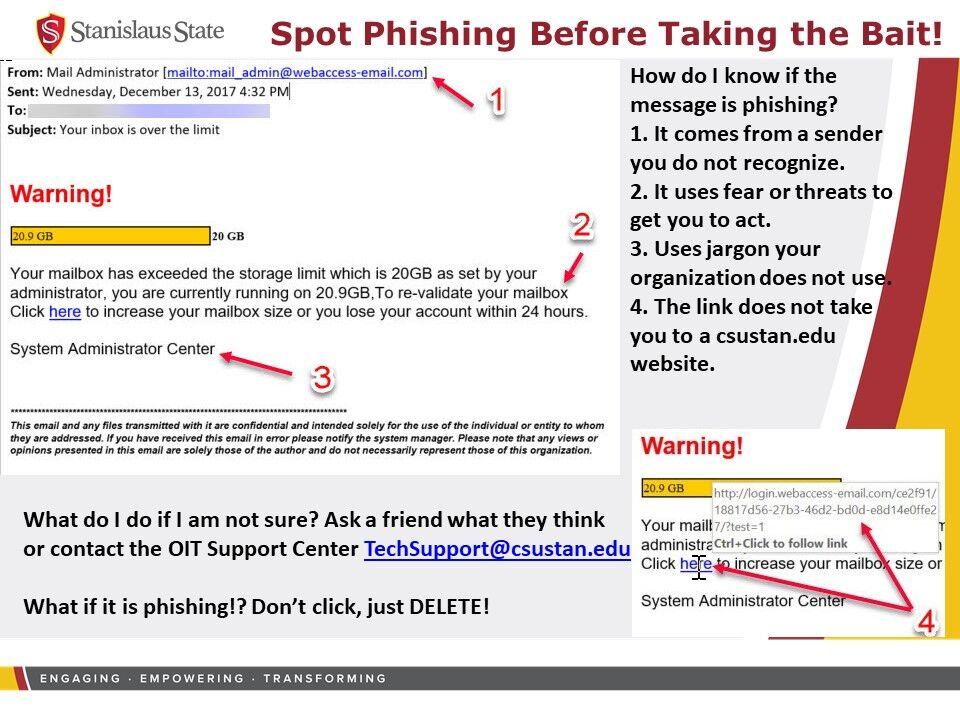
Phishing scams have started to appear more and more frequently in our campus email. In order to avoid these cyber attacks, it may be helpful to understand how to identify them and how to proceed if you do become the victim of a phishing scam.
Phishing scams are defined as, “a targeted attempt to get information. Sometimes it’s a username or password. Sometimes it’s a social security number or some other type of personal information a person wouldn’t normally give out unless they were tricked,” said Nathan Zierfuss-Hubbard, Head of Information Security at Stan State.
When looking to identify such a scam, it was noted that they often involve impersonation or threats, some type of coercion. The most common scams are targeted at students. OIT has seen an increase in requests for students to validate their account, asking them to follow a link and sign in with their Warrior ID and password, in which they are then led to a site under the attacker’s control. Aside from that, there is also an email-based work from a home scam involving an exchange of money where the target receives a bad check in exchange for providing the attacker with a certain amount of money.
Stan State’s Puneeta Salhan (freshman, Math) shared her experience with this second type in the Mary Dempsey scam, mentioning that it took “months after [it happened] to realize it was a scam after I got warned that there’s such a thing as fake emails circuiting the University.”
Salhan was thankfully able to gain assistance from her bank who both verified the check as false and warned her of the risk of online frauds like this one.
Zierfuss-Hubbard also mentioned malware or malicious software-based attacks where one will be asked to click on a PDF to check on something, like a fake package, and this in turn ends up infecting their device.
In all of these cases, the first suggestion offered by Zierfuss-Hubbard was to “reach out to [email protected] and forward them the message you got and ask if it is legitimate” before acting on anything. Emails can also be reported as phishing or junk within Outlook itself which will then report it to OIT.
Salhan advises from her experience that aside from contacting OIT, the receiver may want to “delete the email chain from your inbox and if you provided any information such as your university credentials, consider changing your password ASAP.”
If one has already fallen victim to a phishing scam, there are multiple options available that offer assistance. If the victim has lost money to the attacker, they can report it to www.ic3.gov, where those reports get rolled up and sent to the FBI, as that money loss could possibly be a criminal offense.
Though phishing scams have become more frequent and, in many ways, more efficient, there are some ways to identify them. An easy to spot identifier is within our email address.
Zierfuss-Hubbard points out that recognizing that our email address comes from outside the school system, while the attacker claims otherwise is a sign that something is not right. Along with that, he mentions “they are typically very brief [when] asking you to do something, saying that if you don’t something bad is going to happen, or you’ll get some type of outrageous award.”
There is a sense of urgency found in these types of emails. He claims “speed of transaction is of the essence.” If there is uncertainty to the validity of a message, it is better to ask OIT to verify it or others if they received a similar one, than it is to respond first.
People should also be conscious of forged email headers, ones that look like they are from an actual Stan State account but are not. In these cases, he mentions that “you can forge the from field, but the reply field you typically can’t.”
Similarly, if the “from” header uses what they call the “fancy name,” or a name as opposed to the full email address, “sometimes hovering over that will reveal the real from address.” Both Salhan and Zierfuss-Hubbard emphasize the value of going slow and checking the subject line.
For more information on understanding and protecting ourselves from phishing scams, staysafeonline.org is a useful resource. Furthermore, remember reaching out to OIT via call, email or chat is always an option and their emails will never ask for your username or password. The Warrior page is the only place you should be sent to input those.
Categories:
Understanding and Identifying Phishing Scams
Essence Saunders
•
February 28, 2021
PowerPoint on spotting phishing scams used by Information Security in presentations to employees. Photo courtesy of Nathan Zierfuss-Hubbard, Head of Information Security.
0
More to Discover